A computer virus is a malicious code or a program written for specific objectives such as alter a program or spread itself from one system to another.
Computer viruses are a type of malware that earned their name because of how they spread by "infecting" other files on a disk or computer.
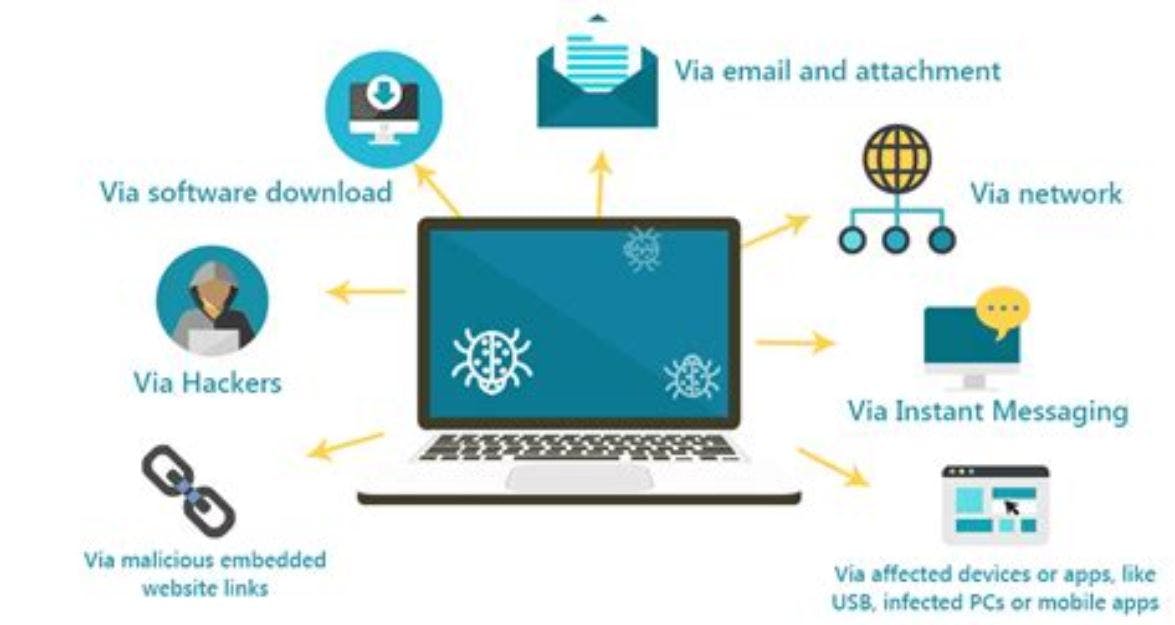
Viruses spread to other disk drives and machines when the infected files are received in downloads from websites, email attachments, shared drives or when carried in files on physical media, such as USB drives or — in the early days — floppy disks.
How does Computer Virus spread ?
Computer viruses may spread as different form such as images, programs, .exe file, word documents, and other file types.
- Downloading malicious apps, files, games
- Email attachments
- Removable hardware such as USB sticks, external hard drives, disc
- Opening or visiting infected websites
- Malvertisements
- Unknown pop-ups
- Malicious links
Phases of Computer Virus Infection
Dormant Phase
The virus is idle in this stage. It might stay 'sleeping' for some time to dodge doubt.
Replication Phase
The virus starts replicating itself. The virus places a copy of itself into other programs or into certain system areas on the disk. The copy may not be identical to the propagating version; viruses often "morph" or change to evade detection by IT professionals and anti-virus software.
Triggering Phase
A trigger occasion gives the infection a sign to act, to begin rejuvenating the programmer's plan. Contingent upon the infection type, anything can be a trigger, including a specific number of infection duplicates or a specific date.
Execution Phase
This is the stage where the infection executes its central goal, which can be anything from taking your passwords to making it difficult to utilize the web.
Types of Computer Virus
Boot Sector
The boot sector virus affects the master boot record, and it is a difficult and tough task to remove the virus and frequently requires the computer to be formatted. It is generally spread through removable disks.
Resident
A resident virus is a type of computer virus that stores itself in the computer memory. From there, it can corrupt and alter your system operations.
Direct Action
Direct Action Virus is also known as a file infector virus, these viruses work by attaching themselves to .exe or .com files. Once the files have been executed or installed. They can use this initial file to access the other files on your computer and start spreading. Direct action viruses can hinder your ability to access files.
Multipartite
Most viruses work by honing in on either executable files or the boot system. The multipartite does both. They can affect nearly every part of the computer by targetting system operations, programs, or folders.
Overwrite
Overwrite virus deletes the infected file, and it is possible to remove and delete the corrupted files, and the user loses all his sensational data. It is mainly spread through emails, and it is mostly designed to damage the file system or an entire application. As the name portrays, it affects the system by overwriting the files with its code and damaging the system’s performance.
File Infector
File infector virus spreads through program files and affects the program whenever it is executed as filetypes. When the file is loaded, the viruses also load along with it. It is also executed whenever the script is loaded.
Macro
Macro viruses are commonly found in programs like Word and Excel. This is because Word and Excel are written in macro language, which the virus attempts to mimic to gain access to your files.
They’re very deceptive, as what can seem like a simple Word document. But, when you click on the document your computer will either become infected right away, or you’ll be redirected to a malicious website.
Polymorphic
Polymorphic virus alters its signature patterns wherever it gets duplicated, and it is difficult to find the affected process. It can convert its attribute into the underlying code without converting the fundamental functions.
Spacefiller Fills
Spacefiller virus fills the space which occurs between the codes and doesn’t affect the file. It is called a cavity virus
Rootkit
The rootkit virus is secretly installed an illegal rootkit on an affected process which opens the gate for hackers and accesses the complete system. The hacker can disable or modify the functions.
What are the symptoms of a computer virus ?
Your computer may be infected if you recognize any of these malware symptoms:
- Slow computer performance
- Unexpected Pop-up Windows Appearing
- Unwanted Programs Start Automatically
- Frequent computer crashes
- Unexplained data loss
- Missing Files and Programs
- Out of Storage Space
- Computer Malfunction
- Blocked From Antivirus Sites
- Advertisements on Web Browser
- Files Turned into Shortcuts
How to Protect Yourself from a Computer Virus
There are a lot of preventative measures that you can take to protect your computer from catching a virus.
Use antivirus protection and a firewall
Get antispyware software
Always keep your antivirus protection and antispyware software up-to-date
Update your operating system regularly
Increase your browser security settings
Avoid questionable Websites
Only download software from sites you trust.
Carefully evaluate free software and file-sharing applications before downloading them.
Don't open messages from unknown senders
Immediately delete messages you suspect to be spam
Using anti-malware and anti-virus software are among two of the most common preventative measures used. Also maintain a backup of your files to minimize the potential permanent damage of a computer virus or malware ,which could corrupt or delete your files.
Firewalls can be helpful in preventing Virus/Malware attacks. It is also wise to always be very cautious when opening emails or clicking on suspicious links, websites, or pop-ups.
If you suspect your Computer already has a Virus
- Start your computer in safe mode and run an anti-virus scan of your entire computer.
- Refer to your computer software supplier’s customer support team to see if they offer any tools or resources to extract the virus from your computer.
- Be sure to delete all of your temporary files in safe mode.
- Use Malware software to scan for additional threats to your computer and security.
